RC IT Services, Partnered with N-Able, brings you :
RMM - Remote Monitoring and Management
Keeping software up-to-date is a critical step in any cybersecurity policy.
Complete patch management in one user-friendly interface
Auto-approve patches when they become available, so end-user devices stay safe and up-to-date.
Set patching windows to update
software without disrupting employees during
times of high productivity
Apply custom settings to individual devices, clients, or sites as needed
View all patch details in “Management Workflow” window, including severity and current and new status—even filter by device type
Third party patching support for the most common application families, including Apple®, Google®, Java®, Adobe®, zip tools, and Skype®.
Continuous updates for Microsoft Windows® (security only and feature upgrades). Approve and install Windows drivers in maintenance windows.
We test and validate patches from Apple and 200+ other vendors before releasing them.
The latest security patches for vulnerable programs, such as Adobe and Java
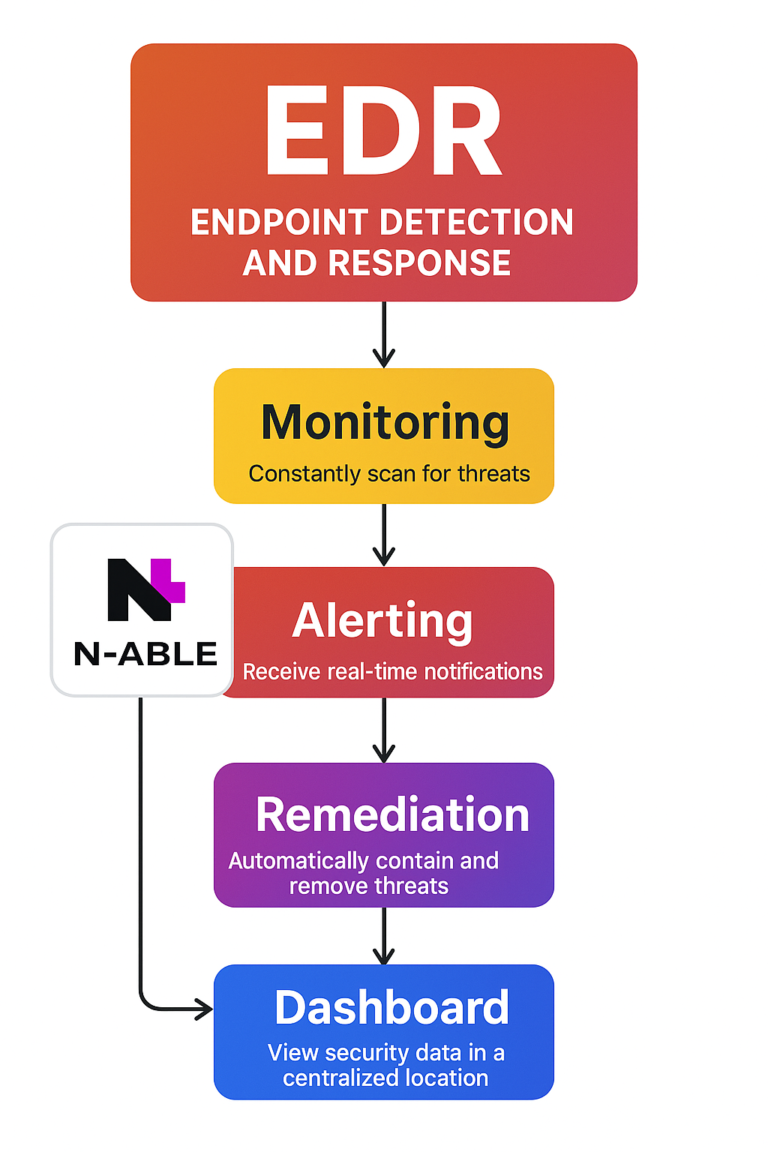
EDR - Endpoint Detection and Response
Detect and respond to cybersecurity threats in seconds
Hand off day-to-day operations to N‑able Managed endpoint detection and response analysts. Ensure ongoing endpoint monitoring and immediate mitigation of malicious events.
Leverage expert interpretation of context-rich threat storylines. Save more time spent on aggregating, correlating, and contextualizing alerts.
Add advanced managed security services to your portfolio and attract more revenue. Take on more customers without hiring more staff.
Finding expert staff to manage SOC operations 24×7 is no easy feat. A managed endpoint detection and response service partner can help address this challenge and save those costs.
MDR - Managed Detection and Response
MDR is a cost-effective and attainable solution for small, medium, or large organizations. Customers can monitor and defend their networks locally, in the cloud, and across the globe.
Review detections and alerts daily and acknowledge them directly on the dashboard.
Security experts can take advanced response action from within the platform, no matter what security technology you invest in.
Monitor organizational accounts for breaches on the open, deep, and dark web.
Assist with automated compliance reporting (e.g., PCI DSS, NIST, and HIPAA)
Provide situational awareness and reporting on current cybersecurity posture, incidents, and trends in adversary behavior to appropriate organizations.
Privilege analysis of every account, system, and group, users can know exactly who can access their most sensitive data.
Professional annual internal and external network vulnerability scans with reports for a clear view of your network (e.g., outdated software, weak passwords, dangerous open ports, etc.)
Get analysis and recommendations for confirmed incidents, including use of timely and appropriate countermeasures.
Cove M365 - Cove Microsoft 365 Protection
• Continuously monitors Microsoft 365 user and application activity
• Builds dynamic behavior baselines for each account using machine learning
• Flags risky behavior like logins from unusual IPs, password spraying, or token abuse
• Suspicious accounts are forced to reset passwords or are temporarily disabled
• Stops threats before they spread to inboxes, files, or shared resources
• Eliminates delays caused by manual review and intervention
• Detailed summaries show what was detected, what was done, and what to do next
• Reduces time spent investigating false positives or vague alerts
• Supports audit logs, compliance documentation, and executive reporting
• Detects changes to MFA settings, service principal permissions, or security configurations
• Monitors enterprise application modifications that may signal persistent threats
• Catches email forwarding rules and inbox changes designed to exfiltrate data quietly
• No endpoint agents or infrastructure to install
• Works with your current Microsoft 365 licensing and security stack
• Gives your team the tools to act quickly and confidently, even with limited resources
Cove Workstation Backup
Protect your desktops and laptops with fast, secure backups using Cove Data Protection. With a reliable workstation backup solution that supports Windows and macOS, you can make recovery seamless and your downtime minimal.
No more relying on full backups. Cove’s TrueDelta technology captures only changed bytes, reducing data transfer by up to 60x and enabling backups as often as every 15 minutes.
Recover files or folders right from the cloud console. Whether you’re restoring a single doc or a full folder, Cove makes the process fast and flexible.
Cove supports bare metal recovery, even for different hardware. This ensures smooth transitions when upgrading devices or restoring after major failures.
Cove secures data in transit and at rest with AES 256-bit encryption. Immutable backups help defend against ransomware and accidental loss so you can trust your data is safe, private, and always recoverable.
Cove Server Backup
Back up your virtual and physical servers directly to our private cloud. Spend less time on administration, while providing better service.
Cove Data Protection helps protect virtual and physical servers with appliance-free, direct-to-cloud backups managed from the same multi-tenant console used to manage backups for workstation and Microsoft 365 data.
Storage in our global private cloud is included, so you can rest assured that your backups are stored off the local network and out of the reach of ransomware. But cloud-first backup doesn’t have to mean cloud-only. Use the hardware or network share of your choice to keep an optional local copy for even faster recovery.
Cove works differently from traditional image-level backup. Our architecture processes changes from within the disk, avoiding the high change rate associated with tasks such as defrag or changed block tracking. This makes incremental backups up to 60x smaller than with image backup products, so you can back up servers as often as every 15 minutes without burdening the network.
Whether you need full-system, application, database, or file and folder recovery, you can count on Cove. Automated recovery testing and the standby image option will help you be prepared for whatever comes – whether natural or physical disaster, cyber-attack, or simple human error.
Beyond this, Cove’s architecture reduces the size of your ransomware attack surface. Not only are your primary backup copies stored off the local network, but Cove is a fully hosted SaaS application, so you can log in from anywhere to begin the recovery process.
Many businesses and organizations rely on Windows servers to make their everyday operations possible, which is why it’s critical that you have secure backups and reliable recovery for Windows. Multiple versions of Windows Server are supported, so you can use one data protection solution for clients at different levels of maturity. You can also count on Cove for customers using Linux, with support for the major distributions.